For the past few weeks, headlines have been awash with reports about ransomware and other disruptive malware. Since malware in a worry for many people, scammers naturally try to profit off this trend. We had our own Tim Berghoff pose as a victim. Read his full report here.
For those who regularly follow our blog, phone scams are not a new phenomenon by any stretch. What is a relatively new phenomenon, though, is the scammers' request to call them, instead of the scammers making "cold calls", where they risk getting people me on the phone who are at home in the field of IT security. My colleague Eddy Willems was fortunate enough to be called by one of those scammers a while back - but instead of being scammed, as is usual during those calls, he even got a job offer out of it.
One method of establishing this contact would be via email or message in a browser window; other methods of establishing this contact might be malvertizing or other malicious software. In this particular case, the user got a message on screen with an "Error Code DW6VB36" which asked him to call a support hotline. This was accompanied by a voice recording that further warned him not to ignore the message, in which case the computer "has to be deactivated" and "a copy of the report would be sent to net security to prevent further damage".
Mode of operation
The first step in any scam is to establish a contact. In cold calls, this initial contact takes place when the phone rings and you answer it. However, recently scammers have started to adjust their mode of operation to the fact that more and more people are aware of scam calls. Past cases have shown that during a call the callers do not waste any time and get straight to the point. They claim to call on behalf of Microsoft (or "on behalf of Windows", as they prefer to call it) or another major company. They then proceed to point out (in various variations) that the user's computer causes big problems which they are there to solve. To this end, they "urgently" need remote access to the victim's computer. They often point out that they (and they alone) can prevent further problems.
Should they be reluctant, some more or less veiled threats are made, such as criminal prosecution, freezing of bank accounts, credit cards or any other online resource. In other cases, the scammer will just lock the user out of the system. As soon as the victim has been talked into granting the "support person" access to their systems, the scammers can do a number of things, including, but not limited to:
- Encrypting the user database using the Syskey tool in Windows - they may claim that they "lock out hackers" in doing so
- Opening normal system log files or the "Services" window and try to convince the victim there are"clear indications for the presence of a virus" - which, of course, they are qualified to remove
- Mention performing a "system scan"
- Offering a "support contract"
Here's the rub:
Any of the "services" the scammers provide will cost money. An often-used strategy consists of providing "support and maintenance contracts" which of course also cost money. In some cases, the scammers install freeware tools on the machine, claiming they are part of their "product" - or they install software which can inflict further damage. If a victim point-blank refuses to make any payments, some scammers proceed to either delete critical files or to render the system unusable. If the user has been locked out of the system (e.g. by locking the user account database), the scam turns into straight-up blackmail, where the scammer will only give the victim access to his or her PC after paying money (if at all).
Dial "S" for Scam
What I did was the following: I set up a machine in a lab environment and connected it to a screen recorder. The PC was connected to the internet using an IP address which is not normally blacklisted by criminals - because criminals are not stupid and know perfectly well which IP address ranges are normally associated with security companies. Native hardware was used, i.e. a "real computer" and not a virtual machine, because some scammers do check whether or not they are lured into a VM. A suppressed caller ID was used to call the toll-free number which was specified in the on-screen message. When calling the phone number, the call was answered by a friendly-sounding female voice with a pretty thick accent. She explained to me what had "happened" and why I was expected to call this number. She then asked me for a phone number that she could call back on. I gave her a cell phone number and she promptly called back. She then proceeded to instruct me to visit a remote support site (in this case "helpme.net", which is a perfectly legitimate remote support site) and told me how to set up the remote connection before handing the call to "one of her highly qualified engineers".
Introducing: Peter from Windows
The engineer who called himself "Peter" also spoke with a heavy accent, but was very friendly. What was less friendly was the fact that he immediately locked the user account database as soon as he logged on. It was easy to follow the steps that he performed. Had I hung up and disconnected at that point I would already be stuck with a nonfunctional machine. He explained to me that he was "securing" the PC against unauthorized access by doing this. Ironically, this is not even wrong, but of course I would suddenly not be authorized to access my own PC.
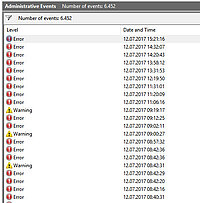
Then "Peter" showed me how many "background viruses" I had on my system by opening the system's Event Logs. All the errors and warnings in there, he claimed, were signs of a virus. The date and time, he told me, represent the time when I had "downloaded" those viruses. But wait, there's more: he then opened a command line window and typed in the "netstat" command. All that command does is list connections to the machine. In most cases there is nothing to see there to write home about, but Peter assured me that all those connections were representing hackers that had access to my computer at any time. On that note, the type of local IP address would have made me curious because no home network that I have ever seen has an IP address that starts with "10.x.x.x". Peter had obviously mixed up public and private IPs as well, but that is just a detail. In any case, it was difficult at times to keep my composure - I was happy that this was not a video call.
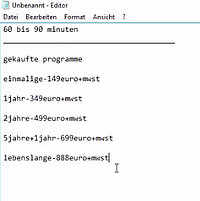
Now it gets bizarre: he began to tell me about "Koobface". This was a malware which made the rounds back in 2010. He claimed that I had that virus on my computer . He awkwardly read me the first couple of lines from the Wikipedia article on Koobface (after doing a quick Google search) and then insisted that something needed doing to fix this problem. For that, he told me that one of their "Third Level Support Experts" would perform a system scan that should take 60 or 90 minutes and required specialized software which needed to be purchased. Now it gets interesting. Peter pulled up a text editor and typed in a price list (see screen shot). For a one-time cleaning he called up 150 Euros. A one-year contract was available for 349 Euros and so on. There was even a "lifetime contract" for 888 Euros plus VAT. The we began talking about payment methods. I immediately told him that I had no credit card (I do, but I certainly wasn't ready to give that to him). He said that this wouldn't be a problem, because they also accepted bank transfer as well as Apple iTunes cards as payment. I tried to coax Peter into giving me some bank details - I even offered him my account details (I have some bogus data that actually checks out for just such purposes) so they could take the money out of the account, but he was very apologetic about the latter - they do not support that, unfortunately. I tried again to get bank details, but Peter all of a sudden insisted on an iTunes card. He started to ask me where the nearest supermarket was and how quickly I could be there. I told him there's a gas station nearby and he asked how long that would take. Now it starts to get odd...I push for a bank transfer, but he tells me that it would cost around 29 Euros more. He was completely stuck on iTunes cards, even though I told him I wouldn't mind the additional cost.
"Silver Partners"
Apparently this did not get us anywhere, so I started to ask him if I couldn't just reinstall the system - there was not much stuff on it anyway, and what little stuff was on there had a backup. He then suddenly the tone got a lot harsher and claimed that not even a reinstall could get rid of the "viruses" that he had shown me - the reason being that "my IP address was infected". I then brought up the idea that I could just ask a friend "who is very good at computers" to help me out and if that failed, I could still call Peter back. Suddenly it sounded like someone else had taken over the call. He asked me in a very pushy manner why I had even called them in the first place if I had a friend who could fix the computer. Truthfully (well...not really) I replied "Because the message on the screen told me to call". It seemed as though he was trying to intimidate me to the effect that I was wasting their time (which, frankly, I did - about 45 minutes of it at that point). After some to and fro, during which he repeatedly pointed out that I was talking to a "Silver Partners of Windows", I suggested again that I could ask my friend, to which he curtly replied "Thank you for your call - Have a nice day!".
Needless to say, after I rebooted my machine, it asked for a password which of course I did not have. Had I called back, they would probably have asked more money to "fix" that problem.
So even though the last person I spoke to wished me a nice day, it would have been anything but - if my predicament had been real.
Why scams work so well
A scammer's best friends are speed, surprise and aggression.
People who are called (or who call actively) are completely overwhelmed with a barrage of threats and fears, mixed in with some techy-sounding lingo. They will also show the user some output in a command line window and claim that the output is a sign of "hackers". All a scammer needs to do is to disable rational thinking for long enough so the victim makes his / her payment. This tried and tested method is also used by ransomware. Since people try to avoid any negative events such as facing criminal charges, financial disaster or loss of important data, they tend to perform any action which they feel averts those events, even if this means giving up credit card details over the phone of on an obscure website. Speed is of the essence for any scammer - they do not want to give victims any time to think, which is why they can become very pushy. If the targeted individual has time to think, the game is usually up.
Cashing in on current events
If certain events have dominated the headlines for long enough, scammers might try to cash in on those. The recent ransomware coverage offers an ideal pretext for such scams. Many people have heard about "hackers" or this thing called "ransomware" by now and they usually know enough to know that it is a bad thing. This is a good foundation for a scam to work. All it takes now is to be convincing and pushy enough on the phone.
What can I do and how can I protect myself?
The steps you can take to avoid falling victim to a scam are quite simple. The crucial thing is to remember those when you are facing a scammer or suspect one.
- Fear and intimidation are the main tools of a scammer.
If the caller threatens negative consequences (legal, financial, technical or otherwise) if you refuse to make a payment or let them connect: hang up immediately.
Scammers usually only work in extremes: you can make the payment and all will be well or you refuse the payment, you go to jail or face a hefty fine.
They also claim that if you don't let the scammer "help" you, the supposed problems will not go away - even if you suggest to rebuild and reinstall the system. - Never, under any circumstances, hand over credit card details on the phone - especially when someone pushes you to do it. The same is true for entering payment data on a website that you are directed to by the scammer.
Do not grant anyone remote access to anyone unless you know them personally and/or completely trust them:
The first thing that scammers often do as soon as they are logged in is to tamper with the operating system in a way that makes it unbootable, if you either refuse payment or cancel the call. - The good news is that the Syskey tool which was used by the scammers in my case will not be supported by Windows anymore after the Creators Update of Windows 10 which will come out later in the year.
- Should the scammer already be logged on: disconnect the network cable immediately.
Do NOT reboot the machine. There is a fair chance that the system will not boot anymore without entering a password which was set by the scammer. Instead, copy and secure all your data to an external storage medium and reinstall the entire operating system. - If you have handed over your credit card details and made a payment, do not waste any time and contact your bank immediately. Have your credit card blocked and the transaction revoked and marked as fraudulent (getting your money back might not always be possible as the transaction has been authorized by you - therefore, the bank assumes that everything is in order).
It is important to note that none of the steps taken by the scammers involve malicious software, at least initially. The remote maintenance tools are perfectly legitimate and widely used and the commands that are entered are part of the operating system and as such, they are also legitimate. For this reason, not even a security suite like the ones from G DATA can protect against this type of attack. After all, scammers are very capable social engineers and try to make people do things on their own (perceived) volition.