Many people make banking transactions online now. And since mobile devices are one of the most popular and convenient ways to shop and make payments, criminals are naturally drawn to this. A current example of a malware that specifically targets online banking shows how easy it is to fall for malware.
Mobile banking, while offering convenience and flexibility, also poses significant security risks. Malicious applications often masquerade themselves as popular applications to trick the users into installing them on their mobile devices. Once installed such rogue applications can steal sensitive information related to banking and can lead to financial loss.
Profiting off the trust of other people
Recently we encountered a trojan that masquerades as Google Chrome. The malware takes advantage of the popularity and trust associated with Chrome to trick users into downloading and installing it. Such malware is often distributed via phishing and spam messages.
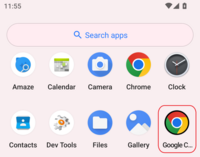
The malware mimics the icon of Chrome, making it almost indistinguishable from the real app, save for a black contour stroke in the logo, which might be easily overlooked when not paying attention. Unsuspecting users might run the malware resulting in their data being stolen and used to their financial detriment.
Permissions galore
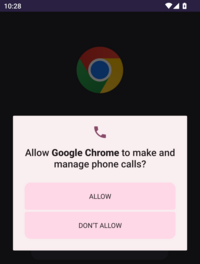
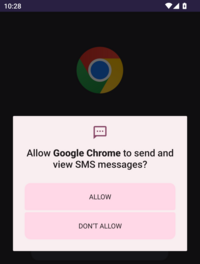
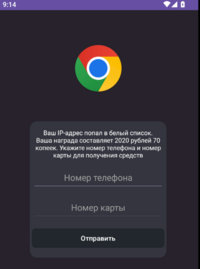
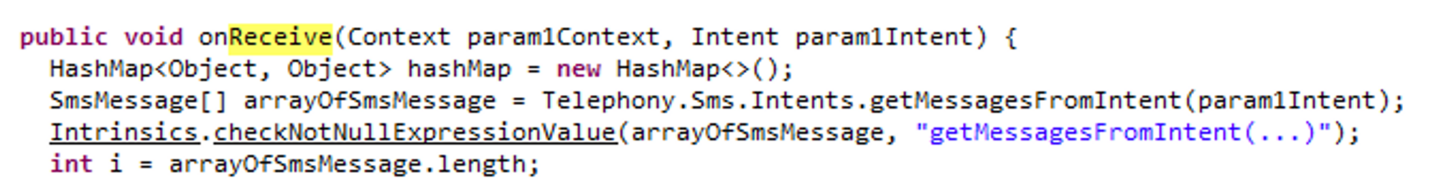
Once installed, the malware application runs immediately. The application requests the user to grant permission for making and managing phone calls. Additionally, it seeks permission to send and receive SMS messages. After obtaining the necessary permissions, the malware falsely informs the user that they've been selected to receive a cash prize, prompting them to enter their phone and card numbers. Following this, the application instructs the user to refrain from deleting the app for the next 24 hours in order to be able to claim and collect the supposed prize money.
Target Demographic
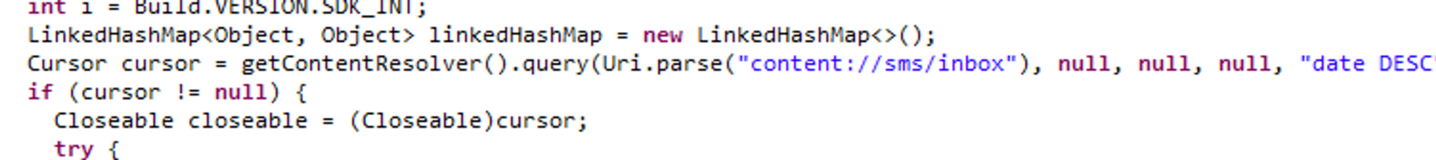
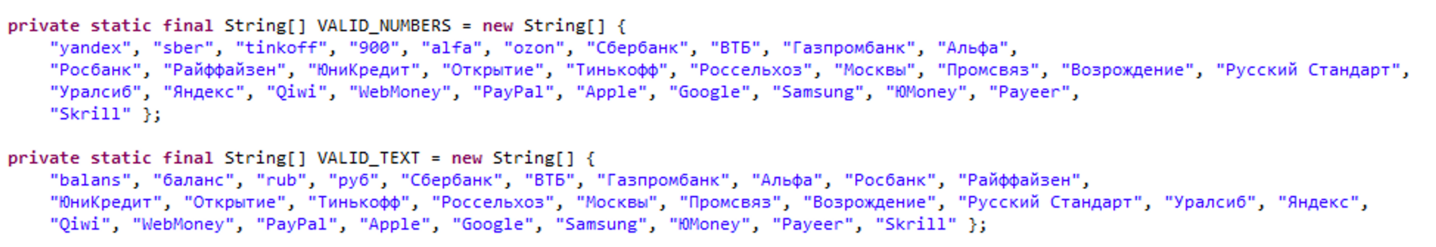
Part of the displayed text is in Russian, and the trojan appears to target a Russian-speaking audience. The malware is called 'Mamont', the Russian word for a woolly mammoth. 'Mamont' is a slang term used to refer to a victim of cybercrime. The malware silently initiates the examination of the SMS messages present on the victim's phone, scanning for both ‘interesting’ senders and predfined keywords within the message body. Its objective is to isolate messages pertinent to a roster of financial service providers such as PayPal, WebMoney etc.
Security at stake
With the aforementioned capabilities, the attacker can acquire the victim's phone number, card number, and intercept SMS messages containing authentication codes necessary to authorize transactions with financial institutions.
In addition to the financial risk, the malware also poses a serious threat to privacy. By combing through SMS messages and forwarding them to the attacker, personal and potentially sensitive information can be exposed. This could include private conversations, personal details, or even confidential work-related information. Therefore, it is crucial to be aware of this malware not only to protect against financial loss but also to safeguard one's privacy.
Indeed, malware threats like the 'Mamont' trojan are not isolated cases. Cyber criminals continually develop new and more sophisticated methods to exploit vulnerabilities, steal information and defraud victims. It is important to stay vigilant, keep software and devices updated, and follow recommended security practices to protect against such threats
How to defend against mobile banking trojans
It's crucial to take steps to protect yourself from the Mamont Spy Banker and similar threats. Even though in this case the malware seems to target Russian speakers primarily, similar malware has been observed which was tailored for other locales and countries as well. Here are some preventitive measures you can take:
- Download apps from trusted sources: Only download apps from official app stores, such as Google Play Store for Android users. Even then, carefully review the app's publisher, reviews, and permissions before downloading.
- Check App Permissions: Always check and question the permissions an app is requesting. Be wary of apps asking for permissions that are not necessary for its function.
- Regular updates: Keep your device and all of its applications updated. Updates often include security patches that can protect against known malware.
- Be cautious of suspicious links and messages: Avoid clicking links or downloading attachments from unknown sources. These are often used in phishing attacks to distribute malware.
- Educate yourself: Stay informed about the latest threats and how to recognize them. The more you know, the better you can protect yourself.
- Sideloading apps: Avoid installing apps from unknown sources.
Remember, no method is foolproof, but these steps can significantly reduce your risk of falling victim to the Mamont Spy Banker.
Information for fellow researchers
424f6a5ccdd9c614836807fab46c2a4cf1eeab7bdbdd2636b20204c585b9bdac