G DATA Layered Security - thoroughly sophisticated IT security
German provider’s Business Security portfolio provides protection against cyber threats by way of a comprehensive security concept.
The level of malware is increasing every day. G DATA expects a total of almost nine million new malware strains by the end of this year. Simple virus protection is not enough to overcome the multifarious cyber threats. Comprehensive security solutions are required that use sophisticated concepts to provide effective protection against online attacks. G DATA Business solutions are designed in layers, in accordance with the “layered security” concept - from the latest security technologies to a comprehensive range of support. It means that cyber criminals have no chance of successful attacks.
Every day, analysts at G DATA discover a host of new malware strains and refined attack patterns that cyber criminals use to go on the hunt for lucrative data. This means that companies need a network solution that has a sophisticated design, is built in accordance with an elaborate security concept and can be enhanced with optional services as required. G DATA has designed its Business portfolio layer by layer, in accordance with this notion.
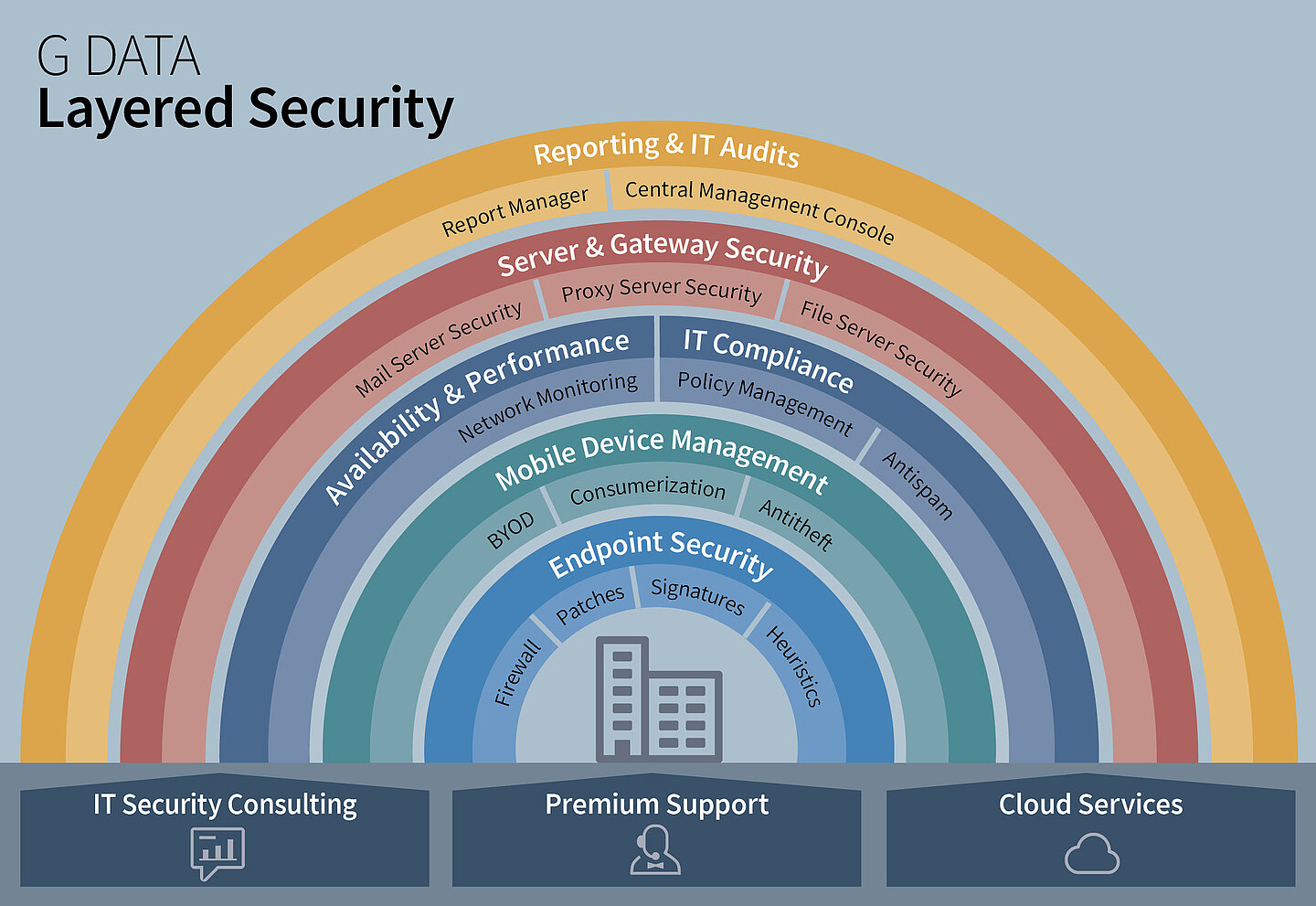
The Layered Security concept in detail
Endpoint Security
Antivirus is an important component of Endpoint Security and combines signature-based detection of malware with the latest technologies for securely blocking even previously unknown malware. This protection is enhanced with a firewall and Patch Management to immediately close security holes in software before they can be exploited for attacks.
Mobile Device Management
Mobile devices are a part of everyday life in businesses and have to be regarded as pocket-sized computers as well as part of the IT security infrastructure. Mobile Device Management reliably secures Android and iOS devices and helps IT managers to accept the challenges of Bring Your Own Device.
Availability and performance
IT systems not only have to be secure, they have to be constantly available as well. Outages of online shops or other elements can quickly become expensive for businesses. Monitoring systems enable a detailed overview of every network component at any time. This leverages a timely response and the implementation of countermeasures before any damage occurrs.
IT compliance
Companies process a wide range of personal and sensitive data on a regular basis, which requires them to adhere to strict laws. Companies can protect themselves against data leakages with Policy Management and other components. As such, IT managers ensure observance of statutory regulations and compliance directives within the company.
Server & Gateway security
The data traffic in a network is often initially processed by a server before it reaches a member of staff. This means that, in the event of a malware infection, the entire IT infrastructure is quickly compromised. G DATA Business solutions protect email, file and gateway servers against malware and other online threats.
Reporting & IT audits
It is difficult for administrators to constantly keep an eye on every component and its IT security status. In G DATA Layered Security, the Report Manager and central management ensure that IT managers can always have access to the latest information.
Consulting, support and Cloud services
Companies can enhance the network solution they are using with optional modules, so the IT manager can subscribe for G DATA Premium Support, for personalised support and service with dedicated contacts. With G DATA Managed Endpoint Security, companies have the option of putting their IT security in the competent hands of a service provider, so they can concentrate fully on their core business. Part of the portfolio here is a Managed Security solution, designed specifically for Microsoft Azure, with which Microsoft Cloud Germany can be used.
G DATA Advanced Analytics also gives companies the option of accessing comprehensive IT security services. These include, for example, incident response, malware analysis and penetration tests.
You can find out more about the G DATA Layered Security concept at: https://www.gdatasoftware.com/business
My data remains in Europe!
G DATA signed a TeleTrust voluntary commitment in 2011. The result - a “No Backdoor” guarantee. With this, the IT company based in Bochum, Germany, undertakes not to provide any holes for intelligence services in its security solutions. G DATA does not leave backdoors open, thus guaranteeing not only the best possible, but also reliable, protection against online threats. This point is very important for companies that take privacy and the forthcoming EU basic data protection regulation (EU-Datenschutz Grundverordnung; EU-DSGVO) seriously. In addition, G DATA promises that the leveraging of personal data and telemetry information is reduced to a minimum. As such, the principle of the EU-DSGVO is already being upheld - and, more than that, the processing of such information and data takes places exclusively in Europe.